Why is cybersecurity vital, and what does it mean?
The protection of internet-connected devices and services against various dangers is known as cybersecurity. It involves safeguarding systems, networks, and data against unauthorized access, cyberattacks, and data breaches. Our Cyber Security Course in Bangalore explains how cyber security has become a major concern for enterprises worldwide due to the increased reliance on technology for personal, professional, and governmental tasks.
Types of Cybersecurity
Cyber security encompasses specialized domains that individually protect specific aspects of digital systems, networks, and data. The following are the primary categories of cyber security:
1. Network Security
Network security is the process of protecting the integrity, confidentiality, and accessibility of computer networks. Its goal is to safeguard the network infrastructure from threats including unauthorized access, cyberattacks, and data breaches.
2. Information Security
Preventing unauthorized access, alteration, or destruction of private data is the primary objective of information security. This includes data that is saved in files, sent via networks, and stored in databases.
3. Application Safety
The primary objective of application security is to shield software applications from vulnerabilities that hackers might exploit. It ensures program security during development, implementation, and maintenance.
4. Endpoint Protection
Devices linked to the network, such as PCs, tablets, and smartphones, are safeguarded by endpoint security. Because these endpoints serve as entry points to the wider network, fraudsters commonly target them.
5. Security in the Cloud
Protecting data, apps, and services stored on cloud computing platforms is the main goal of cloud security. Protecting these systems is essential as more businesses move to cloud environments in order to prevent data breaches and unauthorized access. Take a look at our Cyber Security Online Course.
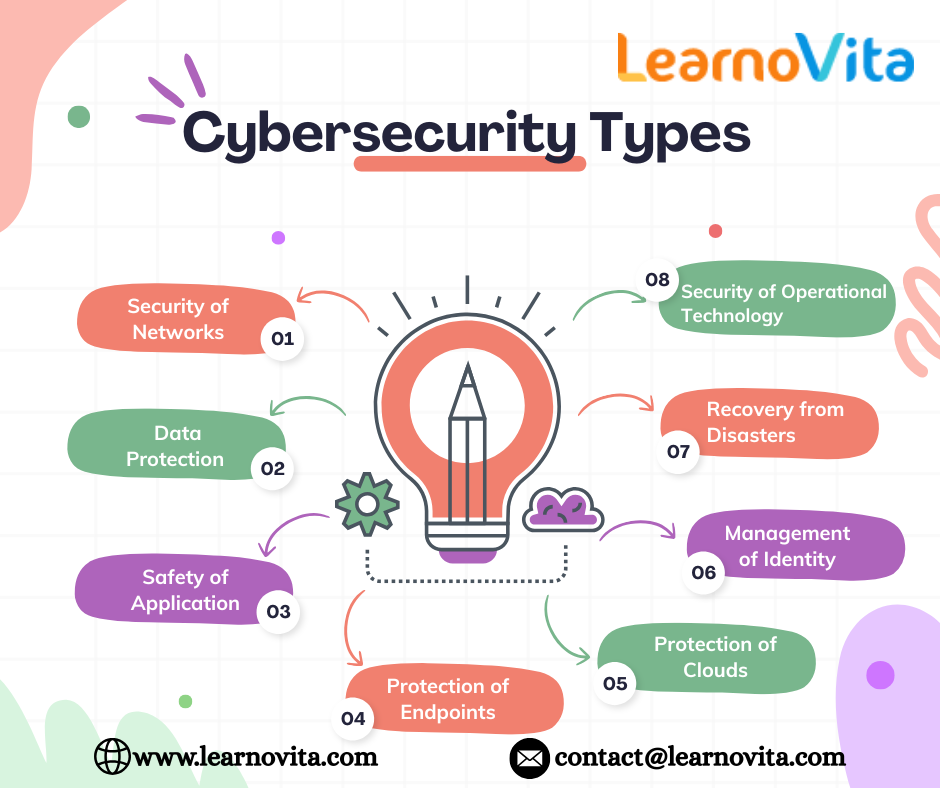
6. Identity and Access Management (IAM)
An essential component of cyber security is IAM, which ensures that only authorized individuals may access particular systems or data. It includes methods and instruments for managing user authentication, authorization, and identification.
7. Disaster Recovery
This type of cyber protection ensures that companies can continue their operations and recover quickly in the case of a cyberattack or natural disaster. It means preparing systems, processes, and people to handle disruptions.
8. Operational Technology (OT) Security
OT security protects the hardware and software systems used in the energy, transportation, and industrial sectors. Since these systems control physical processes, they must be protected from damage or intervention.
Conclusion
Cybersecurity protects our digital life against the growing threat of cyberattacks. As we become more dependent on technology for both personal and professional reasons, protecting sensitive data has become increasingly important. By understanding the principles of cyber security and putting robust defenses in place, we can significantly reduce the risk of cyberattacks.
We are excited to announce the **launch of the Sharkbow Marketplace!** 🎉 Now you can:
- 🛍️ List and sell your products – Open your own store easily.
- 📦 Manage orders effortlessly – Track sales and communicate with buyers.
- 🚀 Reach thousands of buyers – Expand your business with ease.
Start selling today and grow your online business on Sharkbow! 🛒
Open Your Store 🚀 ✖🚀 What Can You Do on Sharkbow?
Sharkbow.com gives you endless possibilities! Explore these powerful features and start creating today:
- 📝 Create Posts – Share your thoughts with the world.
- 🎬 Create Reels – Short videos that capture big moments.
- 📺 Create Watch Videos – Upload long-form content for your audience.
- 📝 Write Blogs – Share stories, insights, and experiences.
- 🛍️ Sell Products – Launch and manage your online store.
- 📣 Create Pages – Build your brand, business, or project.
- 🎉 Create Events – Plan and promote your upcoming events.
- 👥 Create Groups – Connect and build communities.
- ⏳ Create Stories – Share 24-hour disappearing updates.
Join Sharkbow today and make the most out of these features! 🚀
Start Creating Now 🚀- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Giochi
- Gardening
- Health
- Home
- Literature
- Music
- Networking
- Altre informazioni
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness
